Description
Today I am going to talk about VLAN Mapping for Cisco ASA Firewall in Transparent mode. It gives you a fair idea and describes a solution to be able to insert an ASA in transparent mode between two switches to screen multiple VLANs without changing the VLAN numbering scheme on either switch.
In Transparent Mode even though there is only one Layer 3 network for example 192.168.20.0/24 there MUST be two different Layer 2 Vlans (Vlan2 for inside zone and Vlan20 for outside zone). All hosts must reside in network range 192.168.20.0/24
This configuration example explains how to map or translate the VLAN numbers on RouteXP_SW2 for scenarios where the VLANs IDs cannot be renumbered easily after inserting the ASA in transparent mode to an existing topology.
Layout network diagram
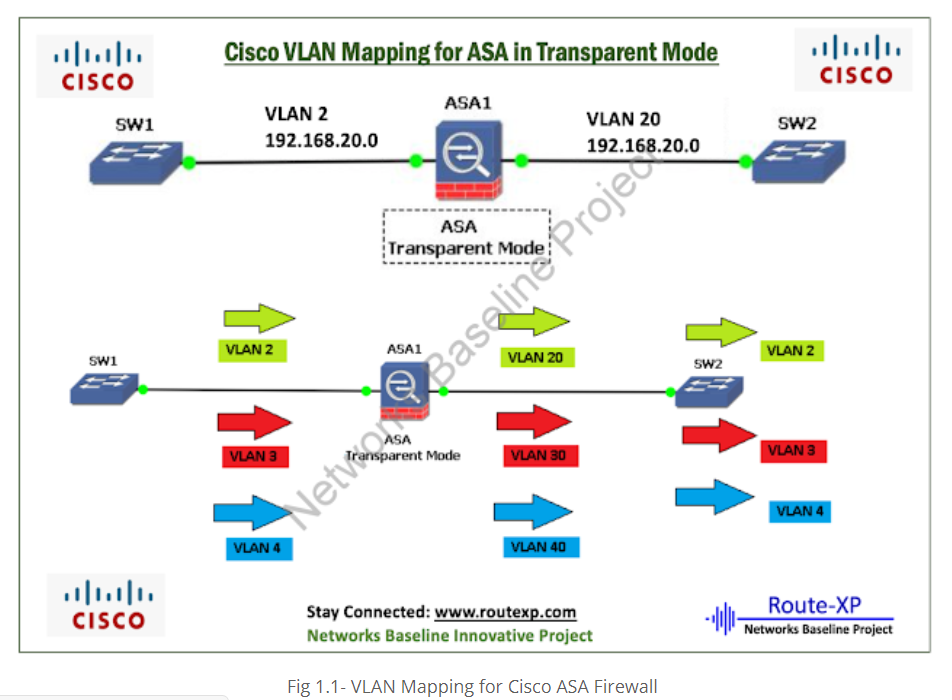
Configuration on Switches and Cisco ASA Firewall
RouteXP_SW1
!
interface GigabitEthernet1/1
switchport trunk allowed vlan 2-4
switchport mode trunk
!Cisco ASA Firewall
!
interface GigabitEthernet0/2
description SW1
no nameif
no security-level
!
interface GigabitEthernet0/2.2
description vlan 2
vlan 2
nameif inside-2
bridge-group 2
security-level 100
!
interface GigabitEthernet0/2.3
description vlan 3
vlan 3
nameif inside-3
bridge-group 3
security-level 100
!
interface GigabitEthernet0/2.4
description vlan 4
vlan 4
nameif inside-4
bridge-group 4
security-level 100
!
interface GigabitEthernet0/3
description SW2
no nameif
no security-level
!
interface GigabitEthernet0/3.2
description vlan 20
vlan 20
nameif outside-2
bridge-group 2
security-level 0
!
interface GigabitEthernet0/3.3
description vlan 30
vlan 30
nameif outside-3
bridge-group 3
security-level 0
!
interface GigabitEthernet0/3.4
description vlan 40
vlan 40
nameif outside-4
bridge-group 4
security-level 0
!
interface BVI2
ip address 192.168.20.1 255.255.255.0
!
interface BVI3
ip address 192.168.30.1 255.255.255.0
!
interface BVI4
ip address 192.168.40.1 255.255.255.0
!RouteXP_SW2
On the allowed vlan list we need to permit the translated vlans 2, 3 and 4 because the VLAN ID in the IEEE 802.1Q tag are mapped (or translated) just before a packet is transmitted and just after a packet is received.
!
vlan 2-4,20,30,40
!
interface GigabitEthernet1/1
switchport trunk allowed vlan 2-4
switchport mode trunk
switchport vlan mapping 20 2
switchport vlan mapping 30 3
switchport vlan mapping 40 4
!Verify
show vlan mapping
nterface Gi1/1:
VLANs on wire Translated VLAN Operation
---------------------- --------------- --------------
20 2 1-to-1
30 3 1-to-1
40 4 1-to-1Good luck
Source : https://www.routexp.com/2019/11/vlan-mapping-for-cisco-asa-firewall-in.html

